With the growing number of cybersecurity threats, online privacy is becoming a huge concern for most internet users. As such, privacy-conscious users will likely prefer using cryptocurrencies to fiat or debit cards for financial transactions.
Sure enough, all financial transactions done using digital currencies are cryptographically secured, protecting user privacy and anonymity. Recipients won’t know your identity or any other personal information unless you buy physical goods and have them shipped to your physical address.
But the security of your transactions is just one part of the whole online privacy equation. As long as your crypto transactions are done over the internet, you still face the risk of being hacked, falling victim to identity theft, and other cybercrimes. Now, this is where a VPN comes in.
But first, let’s understand how a VPN works.
What is a VPN?
A virtual private network (VPN) service is a programmed security tool that encrypts data being transmitted over the internet. The tool secures your privacy by routing your internet traffic through an encrypted channel, making it hard for third-parties, the government, and even your internet service provider (ISP) to intercept or read your online data.
In other words, the sources and destination of your data are masked when using a VPN. This is especially important if you are using public WiFi to access the internet. At this time, you are highly vulnerable to third-party traffic interceptions who may exploit your personal data.
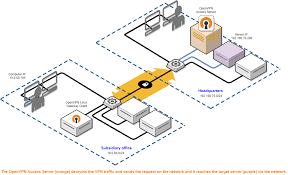
On a regular network, all your online activities can be traced back to you using your computer/smartphone IP address. The address functions pretty the same way as a home address in that it helps identify your exact location. However, when using a VPN, your real IP address is concealed then you’re assigned a new mock IP address enabling you to bypass geo-restrictions. This means your online activities can’t be traced to your exact physical location.
Why You Should use a VPN for Cryptocurrency Transactions
Now that we understand how a VPN works, it’s easy to see how it adds an extra layer of security when using cryptocurrencies. Let’s break down why you need to use a VPN when transacting in cryptos over the internet.
I) Sending Cryptos to other Hot wallets
One of the easiest ways for a hacker to steal your cryptocurrency is by exploiting security loopholes in your hot wallet. Whether you’re sending digital currencies to an exchange site or to another party that you are in business with, your wallet and public key address can easily be identified. With this information, all your transactions can be monitored and even intercepted to gain access to your hot wallet.
The security loopholes stem from the fact that hot wallets and most cryptocurrency transactions are done over the internet. As such, hackers can leverage their expertise to prey on your activities online and even steal your personal information.
Using a VPN, in this case, can help encrypt your online transactions by encrypting data on both ends. That is to say, transactional data between your device as the sender, and that of the receiver cannot be intercepted in any way. Even when using a public WiFi network to carry out the transaction, your activities are hidden from third-parties’ preying eyes.
II) Using Decentralised Apps
On the bright side, decentralized apps such as decentralized exchanges and DeFi tools, do not request users to provide identifying Know Your Customer (KYC) information. From a privacy and security front, users are protected from hacks and personal data theft. But even with this security advantage, users’ activities can still be monitored by identifying their unprotected IP address. You can keep your actual location under wraps by leveraging the ability of a VPN to conceal your real IP address. This way, your activities will be completely invisible, making you less of a target of cybercriminals.
III) Bypassing Internet Firewalls
In the few countries where cryptocurrencies are completely illegal, the government places a geo-restriction, barring any cryptocurrency transactions within the country’s borders. Even those using digital currencies within the country can easily be traced by the government and charged for violating the crypto ban.
However, using a VPN, your connection is routed to a remote server that virtually puts you in a different geographical location. As such, your new location won’t be under the geo-restriction even when you’re actually located in a country that has imposed the geo-block. This way, you can freely transact in cryptocurrencies without detection.
In a good number of countries, using cryptocurrencies is legal. But this doesn’t mean that the government is friendly to the idea of blockchain and cryptocurrencies altogether. As such, the regulators have been known to keep tabs or monitor the transactions of those using digital currencies. If you are concerned about your privacy, the idea of the government monitoring your transactions won’t sit right with you.
Which VPN should you Use
The VPN market is flooded with numerous providers touting their services to be the best in the market. While indeed some offer superior privacy protection, a good number of them should be avoided.
For starters, steer clear of free VPN services for the simple reason that these providers tend to fund themselves by selling users’ private data to governments and advertisement agencies. On the other hand, paid VPN fund their services and infrastructure from the subscription fees paid by the users and have no reason to sell personal data.
Additionally, the headquarter of a VPN service determines its commitment to protecting users’ data. A VPN operating from one of the 14-Eyes Alliance countries can be forced by the law to provide a user’s data since these countries often conduct mass surveillance programs. A VPN service provider based in privacy-friendly countries such as the British Virgin Islands, Panama, and Switzerland can be trusted to keep their client’s data private. In fact, these privacy-friendly countries have imposed laws restricting companies from recording any personal data of the users.
Other useful features you should consider when choosing a VPN include a kill-switch function that terminates your internet connection if you encounter any problem connecting to the VPN. The provider should also have a transparent no-logs policy, meaning that they won’t record any of your online activities. Also, be sure to check if the VPN provider accepts cryptocurrency payments, just to add a little more security and privacy.
Conclusion
There’s no doubt that cryptocurrencies are an ideal way to protect your online financial transactions. While they offer a certain degree of anonymity, users can still fall victim to cybersecurity attacks from the fact that they are connected to the internet when transacting cryptos. So, be sure to use a VPN service to keep your transactions under wraps while at the same time protecting your devices from malware.



