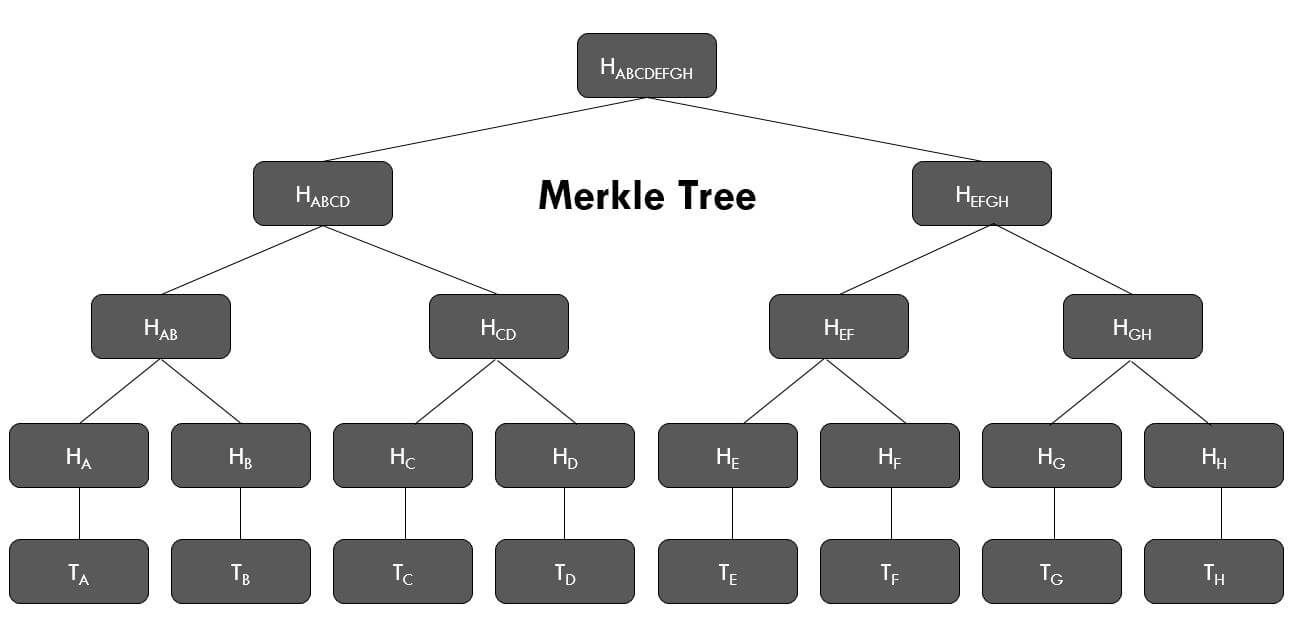
Introduction
Personal identity has been a matter of concern in this digital world. Wherever you go, you have to prove that you are indeed the person whom you claim you are if it is a physical world with some government-issued ids. Mostly all the banks in the world have to have the customary Know Your Customer (KYC)/Anti Money Laundering (AML) laws if you have to open a bank account. The government mandates this.
This process is very costly and time consuming for the banks but is of no personal benefit for the organization. If we have to log in to a website, we input our details or login using Google or Facebook account, given all our personal information to these websites. By this, we are entering our details into a server that we don’t have any control over. Which means they can do anything with our data.
All this process creates a lot of siloes of data, with different government or private organizations around the world. Most importantly, we never have control over what they can or cannot do with the data they collect.
Can Blockchain be a solution for our data?
Instead of giving access to our data to anyone and everyone as the government or organization demands to use their services, what if we create a central repository of data in a blockchain platform. Can this be a solution to secure our data? We can say it’s a yes.
Let us examine how using a Hyperledger Indy project which is a platform being developed for identity management.
Hyperledger Indy
Hyperledger Indy is a decentralized ledger platform for Identity Management. Works on the plenum platform, which is similar to smart contracts but tuned for verifying digital identity. Uses Redundant Byzantine Fault Tolerance as a consensus algorithm. Trust anchors play the role of miners and verify transactions in the platform.
Let us understand Hyperledger Indy using an example.
Let’s say Bob is required to apply for a job, and he needs an academic transcript for the same. Bob gets in touch with his university by creating a unique DID, Distributed Identifier using her public key. This DID verifiable by the trust anchors ascertaining that the request is indeed coming from Bob. If the trust anchors accept the transaction, then only a unique pairwise relationship is formed between Bob and the university. Hence Bob gets the academic transcript using this unique pairwise relationship using DID.
Bob applies for the job by creating a new DID with the company and produce his academic transcript. Again, a unique pairwise relationship is formed in this case because Bob doesn’t want his academic transcript to be leaked. Here the employer can verify the academic transcript with the university with Bob’s consent. But the information cannot be leaked with the same DID to some other employer or some other institution because the DID is already used, and Bob didn’t give his consent to share the information with anyone else. Trust anchors reject the transaction.
This is how unique pairwise relationships can be formed using DID’s and personal data can be protected without leaking the data with the owner’s consent.
Self-Sovereign Identity
A self-sovereign identity, i.e., a user should have complete control over his or her identity. If the user has self-control, then how to prove that the identity being shared is indeed true or not without any third-party intervention? Blockchain is the solution. A platform that is publicly available but individually confidential can be created with issuing authorities given permission to authenticate the identity.
Blockchain stores only cryptographic hash functions, and the concerned authorities can verify even without knowing that it is you who they are validating, they have to cross-check if they indeed issue the proof. If we have to submit an age proof, only age can be authenticated without giving away any other details. A project called Sovrin is already working on this type of identity management.
Blockchain is going to be the future for Identity Management. It has already been proven with the platforms described above.