Introduction
Blockchains use public and private key cryptography to perform transactions in a cryptocurrency network. Public keys are generally widely known and used for identification of the person while private keys are secret keys, which is known only to the person who owns it. Private keys must be kept as secret as they are used for authentication of a transaction.
The Difference
Both public and private keys are a part of the asymmetric encryption of cryptography. The fundamental difference between these two is that the former is used for data encryption and the latter for decryption. Simply said, the Public key converts the message to an unreadable format whereas the Private key decrypts that message and converts it back to the original message. Hence, once the message is encrypted, it can never be decrypted without the help of the private key.
Both private and public keys are large integer numbers represented with a combination of numbers and alphabets. Since we understood the concept of public and private keys now, let us see how they are used in the crypto networks.
How does Public and Private key Cryptography work?
We know that digital wallets are used for sending and receiving cryptocurrencies. Digital wallets are not traditional wallets that store money in a digital format, but they store only public and private keys of the owner of the wallet. Private keys are used to sign the transaction through which the cryptos are transferred digitally. This digital signature is used to confirm the transaction was indeed send by the user who claims to have done the transaction, and no one can alter the same once the transaction is issued.
If someone were to have your private key, they could easily send the money from your wallet to their wallet by verifying the private key. Hence private keys are to be kept a secret from others. This is why it is said if the private key is lost, you lose all your money unless you have a technique to regenerate the private key and transfer it to a replica of your wallet or a new one.
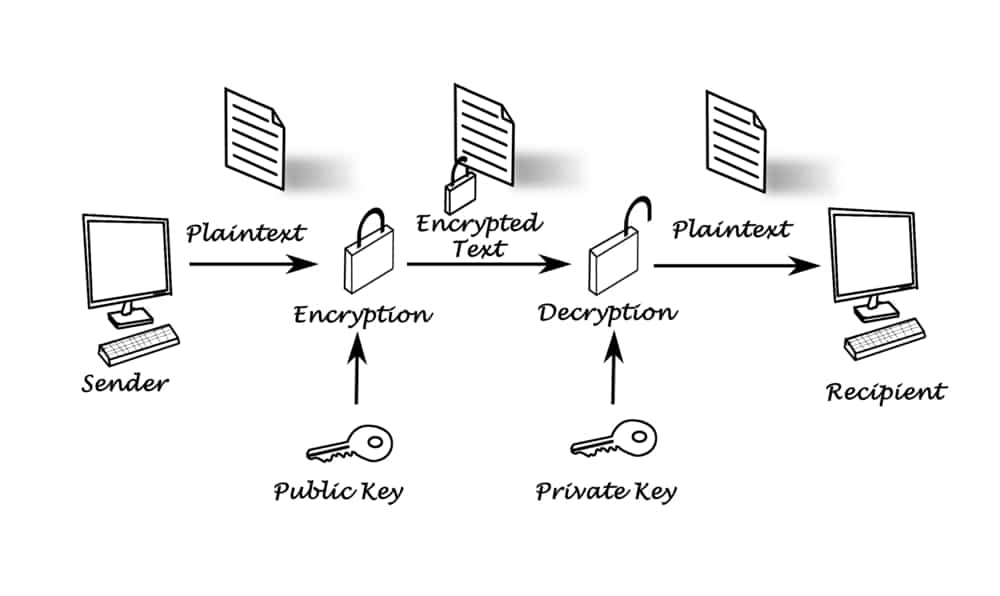
The public key is generated using the private key and some additional information using cryptographic algorithms. This public key is widely known to all the people so that the transactions can be done. One may question if the public key is generated from a private key, can’t we reverse engineer and generate the private key from the public key? The answer is NO. The generation of keys is only one way, but the reverse is not possible since we are using asymmetric cryptographic encryption techniques designed by the National Security Agency of the USA.
Thus, using a combination of public and private keys, one can send and receive the money in digital wallets. Using a public key, one can easily decrypt the digital signature of the user signed using the private key.
Bottom Line
This is how transferring of digital currencies generally works. To end it with a simple example, if Nick wants to send some money say in Bitcoins/Ethereum/Litecoin etc. using his hardware wallet ‘Ledger Nano S’ or any online wallet like Coinbase, what should he actually do? He accesses his private key from the wallet and digitally sign the transaction, and this transaction is sent to the blockchain network. This transaction is verified using the public key to validate if the transaction is indeed being done by the wallet that it is being said, and thus the transaction is successful.
We hope you got a clear idea of what Public and Private keys are. In the upcoming articles, let’s discuss what crypto wallets are and their types. Cheers!

