One of Ethereum’s most anticipated updates in 2018-2019 is the final part called Serenity, which will lead to the shift of the consensus algorithm with Proof-of-Work to Proof-of-Stake. For the miners, this will mean the end of classical mining (proof of labor) and the step towards obtaining an interest in the self-possession of the currency (proof of participation). Good or bad, there’s no definitive answer. Although the PoS algorithm is considered of greatest interest, always viewed from a technical point of view, this consideration may lead to the problem of centralization and pricing. What is PoW and PoS: essence, differences, advantages, and disadvantages, read this article.
PoW or PoS: About Consensus Algorithms
In the spring of 2017, Ethereum developers released some details of Casper’s future protocol. One of the main changes that have been proposed to the protocol, whose publication of the first part was already held in November 2017, will be the transition from the Proof-of-Work consensus algorithm to Proof-of-Stake. This point should first be of interest to those involved in mining. And let the second part of the protocol be postponed, you need to understand the difference between this type of algorithms and what is changed to miners are waiting for. But before that, let’s understand what the consensus algorithm is, in principle, and what they are.
What Is A Consensus Algorithm?
In any network built under blockchain, two types of messages are transmitted: transactions (conventionally, money transfer) and blocks that are made up of these transactions. To make a transaction, it is not necessary the consent of participants outside the system, just know the key (password, identification of the holder of the wallet). Another issue is the blocks, whose order in the transaction log is confirmed by consensus. The biggest problem we’re dealing with on the net is that it’s possible to forward a transaction at the same time between nodes.
Example of the so-called “double expense”. Oleg has 1 bitcoin, which he wants to send, but does it at the same time Alexander and Yana. And if Alexander and Yana do not agree with each other on these transactions (that is, they do not know that a simultaneous shipment was made), then a network problem arises. Therefore, all network participants agree on a transaction log, so that one of Oleg’s operations will be successful, and the second one will be recognised as incorrect. The reason for this problem is obvious, but how to solve it technically is a difficult question.
Byzantine Consensus
The Byzantine consensus is a common definition of the task of the interaction of several participants of the network with each other, located remotely and receiving a task from a single center. And some network participants, including the same center, may be intruders (hackers). In other words, the Byzantine protocol algorithm should provide communication between remote network participants, eliminating fraudulent operations, i.e., transaction security.
The idea of Byzantine consensus appeared in the 1980s. Its essence lies in the following (including fantasy). Byzantium on the eve of the battle. The Byzantine army consists, for example, of four legions that are located at a distance from each other. At a certain point, each of the legion generals receives an order from the executive center to attack or retreat. The development of events is as follows:
If all the legions attack, they win.
If all the legions withdraw, they save the people (also a successful outcome).
If a party attacks, a party retreats, the army suffers defeat.
The work to be done is obvious, but where do we find the guarantee that there will be no traitors who carry out contrary orders? And where do we find the guarantee that the boss will not also be a traitor who sends different orders to his subordinates? Conclusion: Subordinates must comment on the information between themselves, and thus the false data will be deleted. To be precise, they should comment on the information about the number of legions who have been loyal to Byzantium, and draw conclusions about the number of legions of traitors. The task assumes that with N number of generals the traitors can be N-1.
The principle of the agreement is that all loyal subordinates, as a result of the exchange of information, will have to make the same decision, ignoring the information of the general traitor. Let us return to the example. The main feature of the exchange of information is as follows:
Each general sends information on the number of his legion to three other generals. And the disinformation traitor sends the other generals different numbers on the number. In cryptocurrencies, it is an analogue of spam, DDoS attacks, fictitious transactions.
Each general forms a block in which it indicates all four digits received, indicating from whom it was received, and this ready block sends it to other generals.
As a result, each general has in his hands 4 blocks with figures on the number of each legion. And it is logical that for three general figures are the same in the three blocks and only one will have discrepancies.
Thus, the loyal generals reach an agreement, excluding the opinion of the traitor. The example is short, but it clearly shows how network members come up with a single solution, eliminating the fake ones.
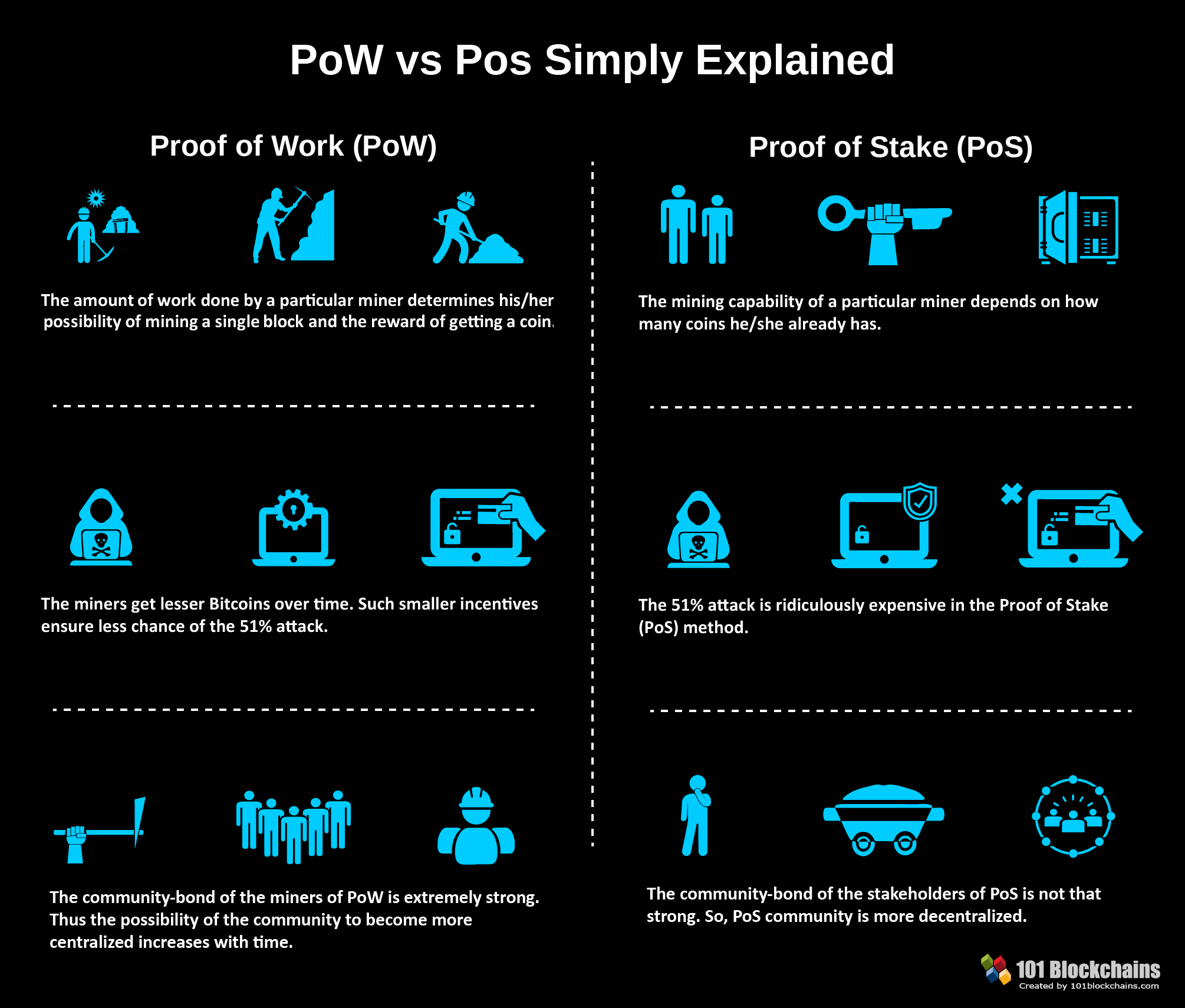
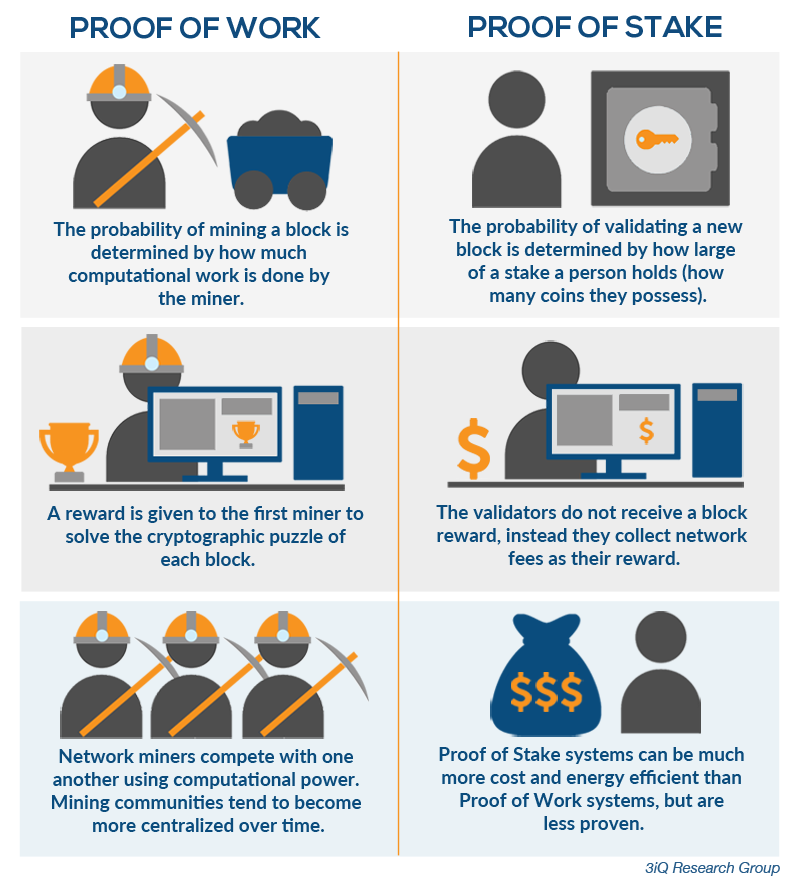
Proof-of-Work Consensus
The Byzantine consensus has a serious problem: the generals know from whom the information comes. That is, there is no anonymity, which is inherent in cryptocurrencies. In the 1990s, a certain version of the consensus algorithm that we’re discussing, maintaining anonymity. In essence, it does not make sense to go deeper, but it comes down to the fact that all the calculations (analyses transmitted to each other in the information network) are made by the PC. To join the network, applicants must complete a certain task (perform a calculation it is not possible for a person, but it is not impossible for a computer), this comes to prove that it is a real user.
The Proof-of-Work algorithm itself (proof of work) is the calculation that the computer performs at the time of mining, while blocking the fake strings and finding the correct transactions.
Distinctive Features of Proof-of-Work
Consensus eliminates the problem of anonymous networks: Sybilla attacks. This situation is what we find when an attacker wants to surround the node of a victim, that is, access all nearby nodes. By seizing the channels of entry and exit of information, you can send false data to the victim. In a BTC built on the PoW algorithm, this possibility is leveled off, as the victim’s node chooses other nodes at random, excluding the victim’s entire environment.
The test does not move to other blocks, that is, it excludes the possibility of stealing from each other (the test is the result of calculations in which energy is spent).
The test cannot be obtained in advance. Each new block will always have a reference to the previous one block, so it is possible to calculate each new test only with the arrival of a new block.
PoW guarantees the integrity of the distribution of the unit’s rewards according to the computer’s capacity. If the power (hash) is 5% of the network, the miner’s computation process creates a certain percentage of the block and receives the same percentage of the reward.
Actual resources, for example, electricity, are spent for the purpose of obtaining evidence, because miners lose the incentive to somehow influence nodes and transmit false information, there is a risk of losing the money invested.
Proof-of-Stake Consensus
If there are many miners in the network and there are also more cryptocurrencies extracted, more power is required for computational operations. Only there are no benefits of these calculations, except for the security and anonymity of the network. Attempts to steer energy in the right direction were in the early stages of Ripple, where miners performed calculations, necessary for different scientific industries (medicine, robotics, etc.), and thus received a reward from developers. But he had to retire.
The second problem in mining is unlimited emission. If bitcoin has this limitation (and BTC extraction is becoming less profitable as the reward for the block decreases), some currencies (for example, Ethereum) have no restrictions. And any unrestricted issuance is charged with depreciation.
The Proof-of-Stake (proof of participation) algorithm deviates from the concept of emission. If in the above-mentioned algorithm, the miner had to prove his presence in the system by calculations, here it is enough that the miner has cryptocurrencies, that is, a participation in the common system on which interests are accrued. In other words, mining as such disappears is replaced by interest.
Other Test Algorithms
The PoW and PoS consensus algorithms use most existing cryptocurrencies. And technically more perfect coins are considered based on PoS. But there are many other mechanisms to protect data, and although these mechanisms are similar to PoS and PoW, they have, of course, their own peculiarities:
Proof-of-Activity is a model that represents the original symbiosis of PoW and PoS.
Delegated Proof-of-Stake is an analogue of PoS, but with elements of vote delegation. Each system member votes for a witness to protect their computer network. The impact on the vote is determined by how many tokens the person has (the more, the greater the impact on the network). The algorithm uses EOS, Lisk, BitShares.
Proof-of-Burn is a model in which the miner sends coins to an address from which they cannot be reliably removed (coin burning). Thus, the miner obtains the possibility of eternal mining, the right to which is played in the form of a lottery among the owners of burnt coins. /li>
Proof-of-Capacity is a model based on the popular idea of “memory as resources”. To participate in the mining process, you need to provide a part of your computer’s memory.
Proof-of-Storage is a similar version of the previous algorithm, with a small difference: the allocated memory is part of the shared cloud storage.
The logic of these algorithms is hard to explain. Since the objective of the algorithm is to ensure maximum network security with minimum power consumption, with which PoS handles very well. Other types of algorithms seem to try to create something of their own, original, but not as effective. And by the maturity of the idea, these algorithms lag behind PoW and PoS.
Consequences of the Ethereum Transitions
And then, again, we return to the same question with which the article began: What can miners expect from future changes? There is still no precise transition plan and the transition is postponed. The road map envisages the start of the transition in Metropolis (Serenity) stage 4. The transition will be smooth: First, according to the PoS algorithm you will check 1 transaction out of 100, then your amount will increase.
Miners do not yet fully understand how the transition from Ether to the PoS algorithm will affect. Criticism of the algorithm sounds relative to the price of a cryptocurrency. If in the Proof-of-Work algorithm the minimum cost of a coin is the amount of energy spent for its extraction, then in Proof-of-Stake the price of the coin is determined by speculators. If the project is not interesting, then the price of the coin will drop to zero. On the other hand, more and more coins go to ICO directly with the PoS algorithm.
The question remains as to the amount of the commission for the possession of coins and their comparability with the profitability of other instruments. There is an opinion that will not be high, and therefore the popularity of Ethereum may be affected due to high risks. In this sense, there are perspectives in Ethereum Classic.
Possible changes may include:
Cost reduction. As the practice of such changes shows, price growth does not occur. On the contrary, miners lose interest in the currency, after which a reduction happens.
Change of mining target. Ethereum mining disappears. And in order to continue using your power, you will have to choose another currency. Or try to join the cryptocurrency project, which offers a fee for computing capacity rental (e.g., Golem).
Change in the correlation of forces. The ownership test can lead to large investors being able to concentrate on most cryptocurrencies, which really destroys the advantage of decentralization.
So far, the feasibility of moving to PoS raises more questions than answers. Analysts agree that the transition to a new algorithm like Ethereum will positively affect, but no one can predict the exact consequences. Cryptocurrency is a new instrument, only to gain experience to fill the potholes.